Usually we focus on SSL/TLS and its role in encryption in-transit. However, equally worth understanding is encryption at-rest. While encryption in-transit (also called in-flight) focuses on secure transmission via an insecure channel, both the sending and receiving endpoint have access to the information in the clear. In contrast, encryption at-rest encrypts data sitting on a hard drive. This protects against physical theft, or an attacker who has already compromised the machine on which the data resides. Arbitrary data is treated as plaintext, and encrypted into ciphertext. A key, passphrase, or both, is required to return the state of the data into something readable. Encryption at-rest can be applied to an entire drive or value such as with Microsoft’s Bitlocker, or it can be more granularly applied to specific files. One very popular tool for accomplishing this feat is GPG (GNU Privacy Guard), which is an open source standard for securing data storage. GPG can be thought of as a suite of individual tools, used for different purposes. One very popular implementation of this standard is GPG4WIN which can be used on Windows systems to encrypt files at-rest.
GPG vs PGP
In order to properly discuss the history of GPG, we must set the scene. In 1991, Phil Zimmermann (one of Newsweek’s "Net 50", the 50 most influential people on the Internet) authored PGP (Pretty Good Privacy). This suite of tools was largely a political statement. We can think of it as the “Signal” private messenger of its era. Remember, at the time computer security was not as ubiquitous as it is today. Zimmermann formed a company around this software, later selling it. This company changed hands several times until ultimately acquired by Symantec in 2010. GPG was created in order to provide an open source alternative to the expensive PGP.
Installing GPG4WIN
GPG4WIN can be downloaded from www.gpg4win.org. Bundled with GPG is Kleopatra, a graphical certificate manager, GpgOL a tool for encrypting emails via GPG and GpgEX, an integration with Windows File Explorer for encrypting and decrypting files.
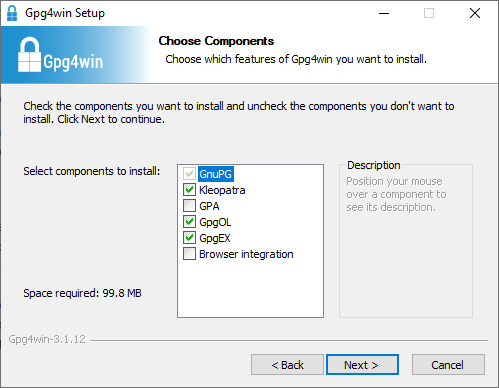
Please leave these defaults selected when installing for the purposes of this guide.
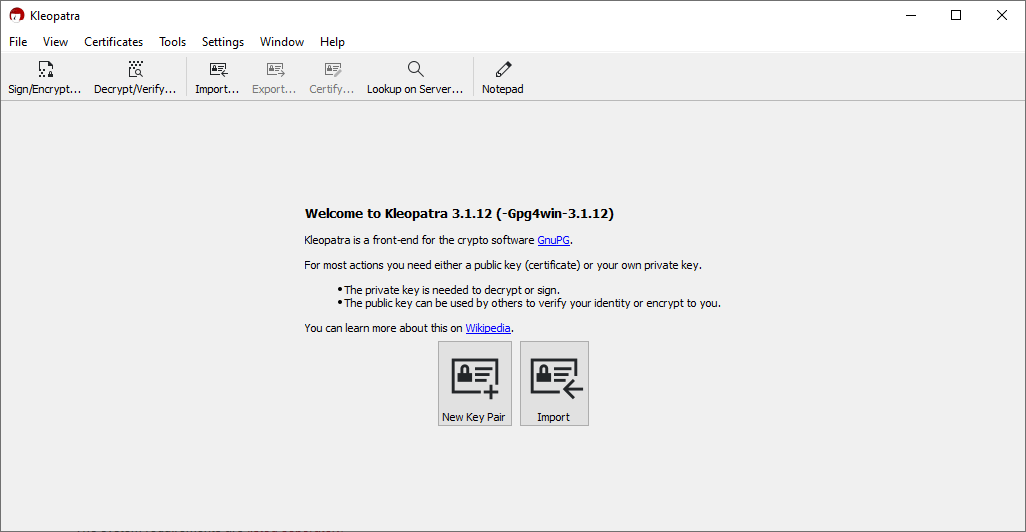
Opening Kleopatra presents us with the above window. The first task worth completing is creating a key pair. Select “New Key Pair”.
Select “Advanced Settings”.
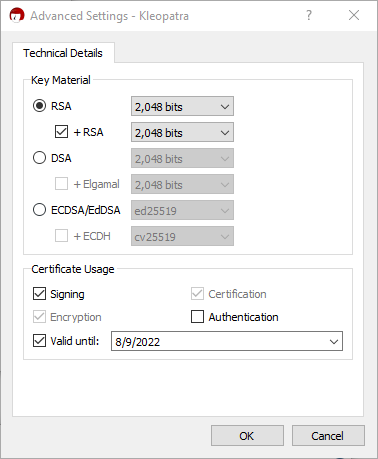
While the program defaults to creating a very compatible 2048 bit RSA key, note that modern versions of Kleopatra are also capable of creating keys that leverage Elliptic Curve cryptography. Those who follow this blog religiously will make the connection that these are the same key generation algorithms used for SSL/TLS when dealing with encryption in-flight.
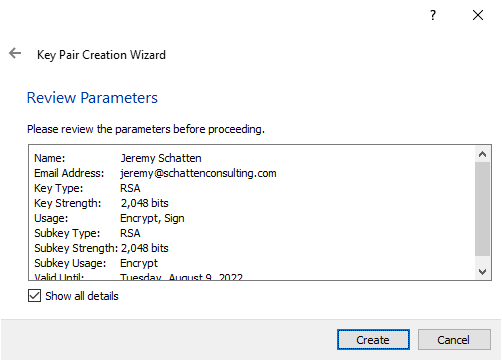
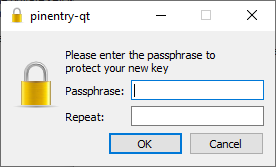
Once you hit “Create”, you will be prompted to set a passphrase on the key. Remember this, without it the private key is useless and all information encrypted with its public analogue is lost.
Each party with which you will communicate will need to already know your public key in order to encrypt data intended to be decrypted by your private key. Exchanging public keys is done as a one-time out-of-band action before secure communication can occur.
Kleopatra serves as our keypair manager going forward. If you were to want to send encrypted information to someone else, first you would need to obtain and import their public key. It will then appear in the list.
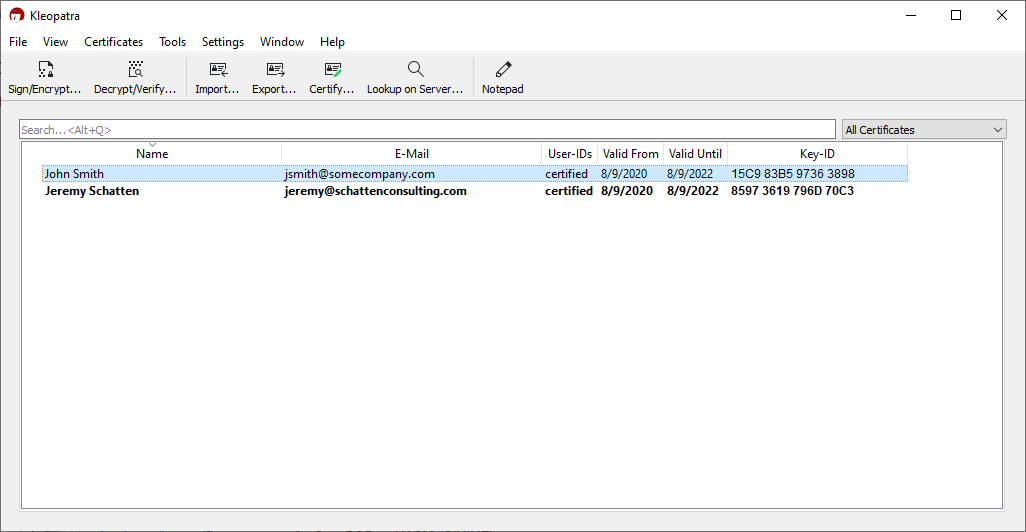
Notice that my key appears in bold. This means that Kleopatra is aware of both the private and public key. John Smith’s entry however is only a public key. I can encrypt files that only John can read, and sign them with my private key so that he knows that they were without a doubt from me. This is accomplished via public key cryptography, the same used during the first phase of SSL/TLS.
Select “Sign/Encrypt” from the top bar, and navigate to a file you want to encrypt.
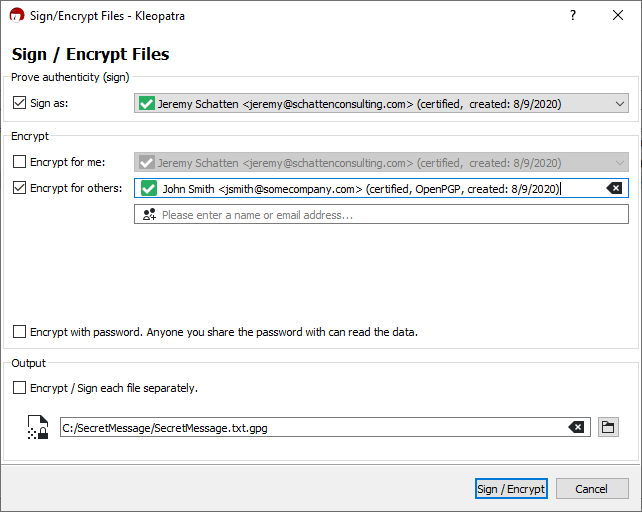
Selecting the above options will generate a file “SecretMessage.txt.gpg” which is an encrypted version of SecretMessage.txt. It can safely be sent over an insecure channel, even without using SSL/TLS! Only John’s private key can decrypt this message.
Note that you can also encrypt a file such that anyone with a password settable by you can decrypt that file.
Let’s say instead the goal is to encrypt data for your own consumption at a later date. Simply select “Encrypt for me:” instead at the prompt above.
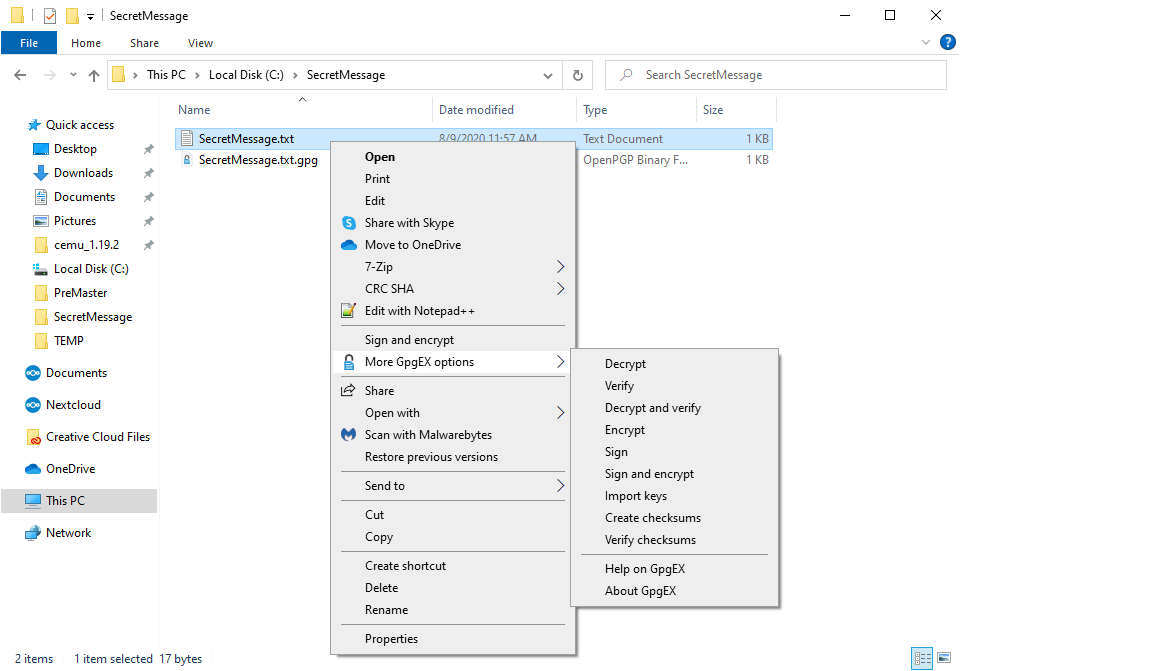
If GPGEx is installed, a new option will appear in your Windows explorer context menu. The same option can be triggered without even opening Kleopatra!
Conclusion
GPG4WIN is an excellent tool. It provides a mechanism for securely encrypting and decrypting files, as well as managing public keys of individuals or organisations you may elect to communicate with. In a perfect world, it, or something like it would be the norm. There are two barriers to widespread adoption. Firstly, GPG requires that public keys are exchanged in advance. This isn’t a lot to ask of developers and Systems Administrators, but to your average user, keeping track of public and private keys can be cumbersome. Additionally, GPG4WIN requires that software is installed. It’s very likely that if it were built natively into the Operating System, it would enjoy more widespread use. Still, there are many excellent uses for GPG4WIN. It’s an excellent way to encrypt backups, especially of sensitive data like private key material. Combining GPG and email is a natural fit, because with SMTP you cannot guarantee as the sender that data is encrypted end-to-end. (SMTP by its very nature may traverse multiple servers not in your control, unlike HTTP which is endpoint-to-endpoint communication). What are some ways in which you’ve used or will use GPG4WIN?
